
Foresite (a global service provider) delivers an array of managed consulting and security solutions to help their clients meet compliance and information security initiatives.
These solutions let organizations proactively identify as well as respond to cyber-attacks and breaches where they occur, and remediate them.
Once you know what managed detection and response (MDR) is, the next question is often if the cost is worth the benefit for your organization.
Here's how to decide if you should invest in an MDR solution.
Enterprises generate millions of log alerts every day. Foresite helps rule out that noise and determine what data is meaningful providing you with actionable information that will help you respond and protect against damaging security threats.
Organizations like yours continue to fight an asymmetric battle against cyber attackers. These attackers are well-funded, sophisticated and well-organized. They use techniques that are highly targeted and which leave technology-only security strategies exposed. To stop them, you need to understand them – how they work and think, and what they want.
Software that’s outdated and devices that are unmanaged can leave your staff, organization and yourself wide open to cyber threats. Foresite can help you manage your organization’s security infrastructure and also protect your critical assets so you can leverage their technology investments sooner and longer.
Cyber attacks can severely impact your company’s bottom line revenue and damage your company’s reputation. Our managed incident response solutions help you stop the attack, assess the damage, and mitigate the impact to your business.
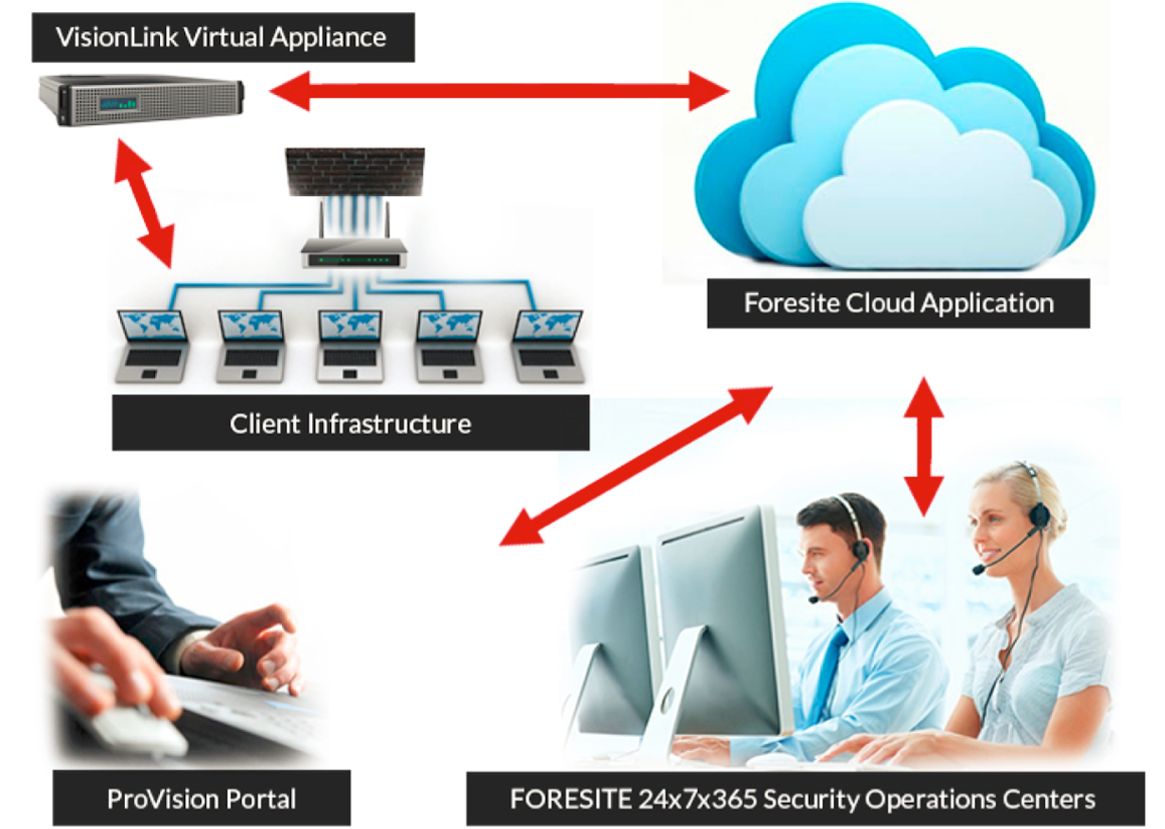
Foresite’s proprietary management platform is cutting-edge, and will put you in your business’s driver’s seat for business security and data operations. It’s designed to meet today’s moste stringent industry standards all with ease of use and flexibility that is unmatched.
Foresite’s experience and education differentiate us from their competition. It’s vital that, as technology evolves – that businesses in this industry work harder and harder to stay informed and keep ahead of the inevitable curve. Foresite That’s why we do our best to earn each and every certification relevant to our field of business – as well as yours. Below is a list of our various certifications and credentials.
Organizations like yours are under the constant threat of cyber attack. These continuously evolving attacks get more sophisticated and persistent. Then, as an organization’s technology needs keep increasing, your potential vulnerabilities and entry points can also increase. To deal with such persistent threats, organizations must implement the most advanced security testing policies. Waiting until an attack has begun can mean the difference between a huge crisis vs a small issue.
In any security system, the weakest link is usually the human element. Scrupulously tight security systems will be defeated by just one person who acts in a manner that’s unauthorized. An attacker will frequently take advantage of an end user’s lack of security awareness as well as the innate desire most of us have, to be helpful
It’s easy to find data compliance confusing? So many acronyms for various types of data, industries, and required methods of storage make regulations difficult form someone without technical expertise to interpret. Foresite makes these complicated compliance issues easy for non-technical executives to understand. You’ll be walked through your current compliance operations and get suggestions for improvement.
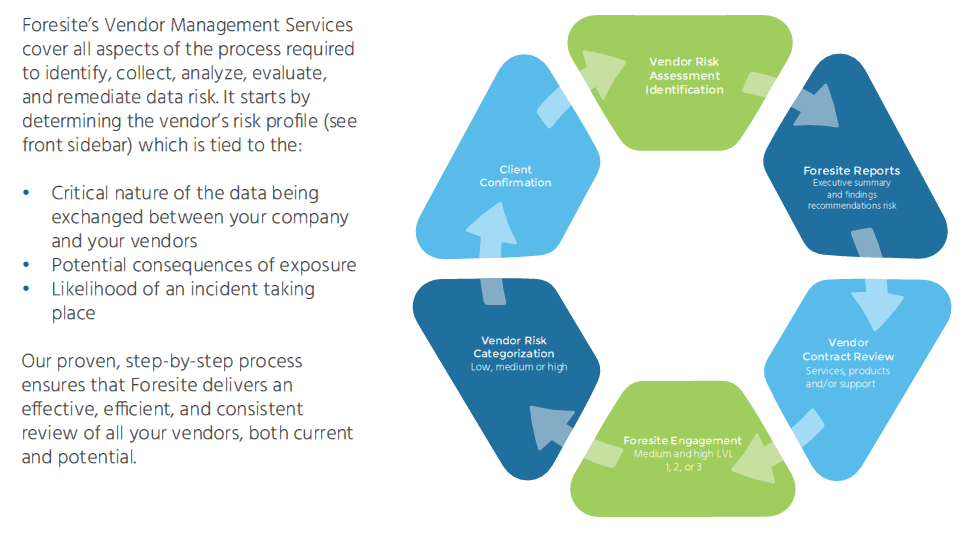
Many organizations partner with third-party vendors as an essential part of their business.
It lets them to keep their costs down, reach larger segments of their market and focus on core areas of theie business. However, are you aware of the risks that those relationships could possibly expose your organization to?
